Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Announcing Social Trends: Use social media for security intelligence
We are excited to announce the availability of Social Trends, adding social media intelligence (SOCMINT) to Snyk’s vulnerability data to help development and security teams prioritize vulnerabilities more effectively. Given the size of vulnerability backlogs facing organizations today, finding and fixing security vulnerabilities in a timely manner is a monumental task. There simply are not enough hands on deck to triage and tackle all the vulnerabilities on the list.
Kubernetes Quick Hits: Use SecurityContext to drop unnecessary Linux Capabilities
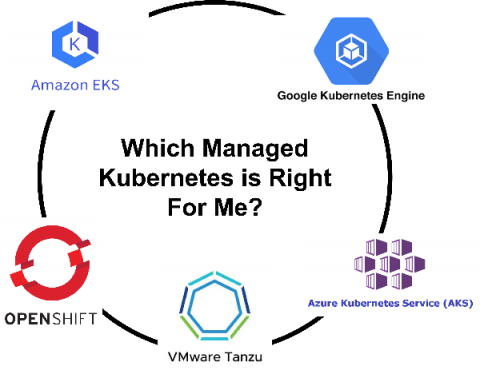
Which Managed Kubernetes Is Right for Me?
Kubernetes helps with scaling, deploying, and managing containerized workloads, facilitating a faster deployment cycle and configuration management—all while providing improved access control.Kubernetes is also a CNCF project, meaning it’s cloud-native and can be easily deployed through any cloud provider. This blog will compare on-premises, or self-hosted,Kubernetes clusters to managed ones, as well as outline your options for Kubernetes in the cloud.
100+ Server Security & Best Practices Tips on Securing a Server
Servers are the backbone of an organisation’s IT infrastructure as they provide both information and computational services to its users. And because of their critical role, servers are always a prime target for hackers looking to exploit any vulnerability they can find, leading to data breaches and financial and reputational damage.
The Complete Guide to Prototype Pollution Vulnerabilities
Prototype Pollution is one of the less known vulnerabilities in the security community. Researchers started to discuss it as a potential attack vector around 2017, and the first vulnerabilities were found in the wild at the start of 2018. In this article, we’re going to take a deep dive into what Prototype Pollution vulnerabilities are, and how they can be mitigated.
SAST tools speed comparison: Snyk Code vs SonarQube and LGTM
We’ve been asked to provide a comparison of scan times between Snyk Code and two common SAST tools: LGTM and SonarQube. For our research, we made several assumptions, but we’ve shared the details in order to be transparent.
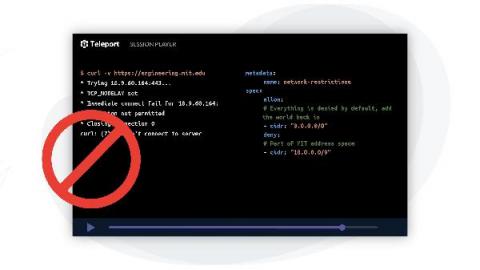
Preventing Data Exfiltration with eBPF
To keep your business secure, it is important not only to keep the hackers from getting in but also to keep your data from getting out. Even if a malicious actor gains access to the server, for example via an SSH session, it is vital to keep the data from being exfiltrated to an unauthorized location, such as IP addresses not under your organization’s control. In considering a solution to protect against data exfiltration, it is critical to note that one policy does not fit all.
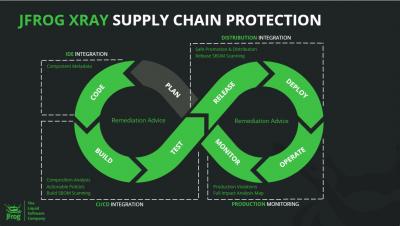
Vdoo & JFrog - Enhanced Security From Code To The Edge
Four steps for hardening Amazon EKS security
In the first part of this blog series, we explored deploying Amazon EKS with Terraform, and looked at how to secure the initial RBAC implementation along with securing the Instance Metadata Service. In this second post, we’ll look at more best practices to harden Amazon EKS security, including the importance of dedicated continuous delivery IAM roles, multi-account architecture for Amazon EKS cluster isolation, and how to encrypt your secrets in the control plane.