Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
The Importance of Prioritizing Product Security
Achieving comprehensive security for the products delivered and deployed by organizations is becoming more difficult, due to a variety of factors. A key one is the growing volume, variety and complexity of software and connected devices in use. Another is the overwhelming risk of inherited software supply chain exposures. The result: Companies struggle every day to provide software with optimal security and protection against malicious activities, takeovers, data theft, and commercial sabotage.
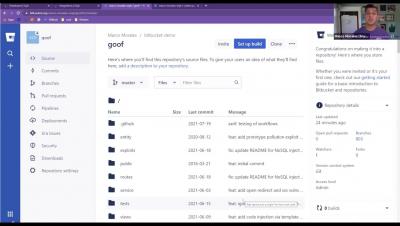
Getting Started with Snyk Inside Atlassian Bitbucket Cloud
Panel on Shift Level with CISO's Part - 2
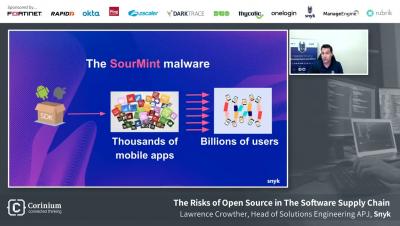
The Risks of Open Source in the Software Supply Chain with Lawrence Crowther, Snyk
Synopsys partners with Wind River with its industry-leading Coverity static analysis solution
The Coverity and Wind River partnership supports developers with fast-turn CI/CD workflows and container-based development. Highlights.
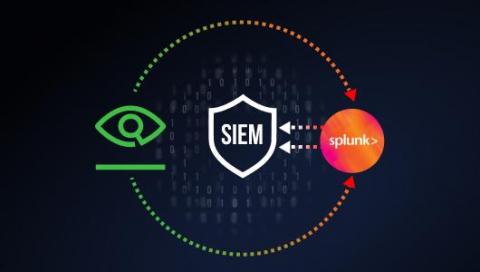
JFrog Xray + Splunk + SIEM: Towards Implementing a Complete DevSecOps Strategy
Making security an intrinsic part of a DevOps pipeline is a “must-have” for organizations looking to secure their applications earlier in the development process. The combination of JFrog Artifactory and JFrog Xray enables organizations to build security into all phases of their software development lifecycle, so they can proactively detect and mitigate open source software (OSS) security vulnerabilities and license compliance issues that impact their software.
Catalogic's CloudCasa Launches Kubernetes Persistent Volume Backup to Cloud Storage
The Open Policy Agent SDK Overview
Authorization is a critical part of developing any application. When building an app, at some point you will want to control the data and views that a user or system has access to, and one way you can do that is by writing authorization directly into your app. However, over time this can be challenging to manage because when you make changes to your authorization policies you also need to make changes to the application.
So You Want to Become a Sales Engineer?
Those of us that work with technology get this question a lot: “What do you do?” “I work in technology — more specifically, I work as a pre-sales engineer.” Sound familiar? Working in IT can mean a lot of different things, and to those outside of this world, it quickly becomes deeply technical and complicated to explain to non-IT people. Even explaining what you do to IT people can become complicated.