Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Learning Equality Micro-interview with Snyk Impact
Fast Forward Micro-interview with Snyk Impact
Develop for Good Micro-interview with Snyk Impact
Styra DAS: Building for the Open Policy Agent community
It’s been a great year so far for the Open Policy Agent (OPA) project and community. OPA achieved graduated status in the Cloud Native Computing Foundation (CNCF) in February and is quickly nearing 100 million downloads! With all this growth, we were excited to see the results of the second annual Open Policy Agent user survey. As I mentioned in my post on the Open Policy Agent blog, we survey the community to help better steer the project's long-term roadmap in the right direction.
A (soft) introduction to Python dependency management
Python has been deemed as a “simple” language — easy to use and easy to develop scripts to do numerous tasks — from web scraping to automation to building large-scale web applications and even performing data science. However, dependencies are managed quite differently in Python than in other languages, and the myriad options of setting up an environment and package managers only add to the confusion.
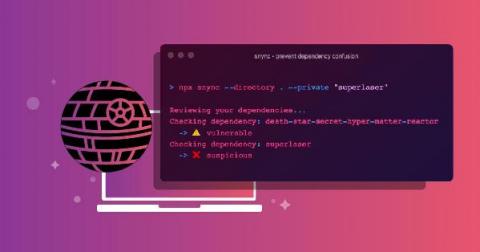
Detect and prevent dependency confusion attacks on npm to maintain supply chain security
On February 9, 2021, Alex Birsan disclosed his aptly named security research, dependency confusion. In his disclosure, he describes how a novel supply chain attack that exploits misconfiguration by developers, as well as design flaws of numerous package managers in the open source language-based software ecosystems, allowed him to gain access and exfiltrate data from companies such as Yelp, Tesla, Apple, Microsoft, and others.
DevSecOps Road Trip UK stop - Andrew Martin & Lili Kastilio
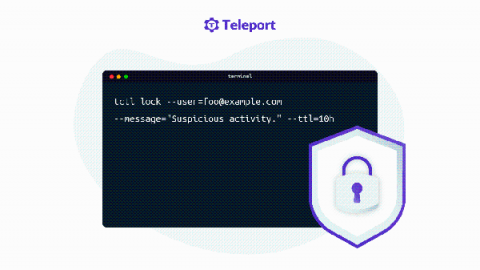
Security Incident Containment with Teleport Session and Identity Locking
What would you do when a security incident is detected? Shut down the servers? Pull out the power cord from the data center? When an incident is detected, both the incident method and the time required to contain an incident are essential to limit the damage. The slower you are to react, the more damage an incident would incur. And a service downtime to contain an incident can cost businesses even more than a security incident itself.