Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Tools for infrastructure drift detection
Predicting infrastructure drift is like predicting snowfall in winter… you know it will happen at some point but you can’t predict exactly when. And just like snowfall, having a way to detect it as early as possible is what will make you the most prepared and your infrastructure more secure! In this article, we’ll explore the principles of drift detection, the different kinds of drift and why they happen, and tools to help detect drift with a simple example.
How to build collaboration across security and DevOps teams-and why it's business critical
For security and DevOps teams, staying a step ahead of the competition comes down to staying in lockstep with each other. Whether that competition takes the form of a threat actor lurking on a network or a rival company taking new products to market, collaboration can help security and DevOps teams better protect their organizations and develop innovative technology solutions.
Kerberos Attacks - All You Need to Know
Build a software bill of materials (SBOM) for open source supply chain security
More than ever, developers are building web applications on the foundations of open source software libraries. However, while those libraries make up the software bill of materials (SBOM) components inventory, not all developers and business stakeholders understand the significant impact on open source supply chain security that stems from including 3rd party libraries.
SSH into Docker Container or Use Docker Exec?
SSH has always been the default mechanism to get remote shell access into a running Unix or Linux operating system from a terminal client to execute commands. While SSH is familiar, Docker provides more lightweight and easier-to-use methods that don’t require running your container with an SSH server. This post will explore two methods to get shell access into a Docker container using OpenSSH and the docker exec command.
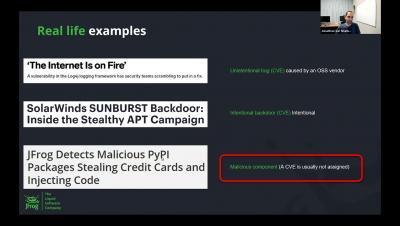
Identifying and Avoiding Malicious Packages
Artifactory Integration - Plugin Upgrade
Announcing Snyk free security for open source projects
Why Single Sign On Sucks
A month ago I tweeted about my annoyance with SSO or Single Sign On. While single is in the name, I’m required to “single sign on” multiple times a day. I’m not the only one; the tweet went viral with over 25k likes and 2 Million impressions. The tongue-in-check tweet created a lot of fun responses and more rage against SSO user experience than I expected. SSO was meant to solve password fatigue but we got something worse.