Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Project Pyrsia: Securing the OSS Supply Chain
Integrating Dependency Management Into Cloud Services: The Mend-AWS Partnership
The ongoing growth in the adoption of cloud services poses escalating opportunities and risks in equal measure. The increased capacity and scalability of cloud environment lends itself to an accelerated pace and higher volume of software and application development than ever before. This trend brings into play a huge increase in the number of software components and dependencies that developers use in their code bases.
Announcing Mend SCA for Bitbucket Cloud Integration
We’re proud to announce that Bitbucket Cloud users can now unlock the full power of Mend for automatic detection and remediation of open source risk. With the release of our new Bitbucket Cloud integration in the Atlassian Marketplace, Mend now makes it possible for developers to find and eliminate vulnerabilities, all while staying in their Bitbucket Cloud repositories.
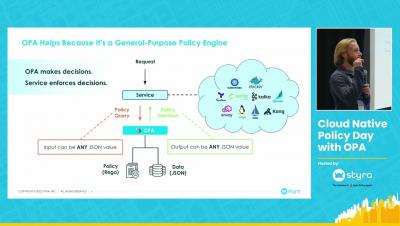
Policy as Code with Azure API Management (APIM) and OPA
A common use case for Open Policy Agent (OPA) is to decouple authorization from the application. This enables policies and decisions to be managed centrally and lifecycled independently to the application. For application use cases, OPA can be integrated at the API Gateway, Service Mesh or Microservices layer or any combination of these.
2 million .git directories exposed! Why .git folders are sensitive & how they are leaked publicly
Meeting PCI DSS Compliance with Styra DAS + Kubernetes
DevOps and platform teams are more strained than ever, and as a result, need better tools than ever. These teams are required to develop, provide access to, and secure a number of resources — while remaining good stewards to application developers. Beyond that, they are often tasked with overseeing their organization’s shift to the cloud. And as that shift takes place, DevOps teams will need to shift their compliance standards to the cloud.
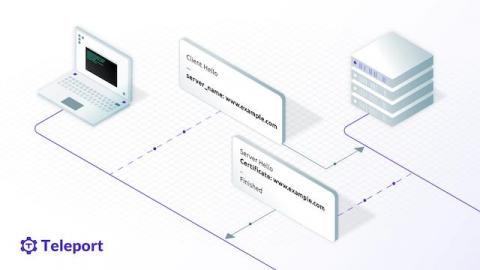
TLS Routing Support for Teleport Behind an AWS Application Load Balancer
In Teleport 8, we introduced the TLS Routing feature that can multiplex all client connections on a single TLS/SSL port. Recently we've added support for TLS Routing for Database Access when Teleport is deployed behind an AWS Application Load Balancer (ALB). In this article, we will take a deep look at the problem with Teleport behind an ALB and how we solved it.