Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
Take GitHub threats seriously: The largest code-sharing platform is extending your attack surface
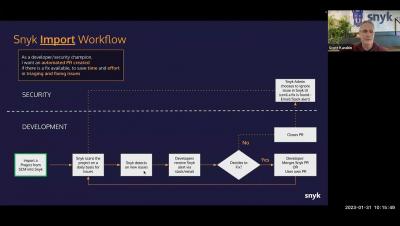
Snyk Workflows - Basic Workflows (IDE & CLI)
Quick Start Guide: Integrate Veracode in Your DevOps Pipeline
For today’s DevSecOps teams, the demands continue to intensify. Application portfolios and codebases continue to grow, while cyberattacks remain an ever-present danger. More than ever, it’s vital to ensure security gaps are identified and addressed with maximum speed and efficiency. In order to do this, you need to establish a continuous feedback loop on security threats, so you can realize optimized, sustained results – which is exactly how Veracode helps.
Application Security Requires Concerted, Continuous Efforts
According to Forrester Research, applications are the top cause of external breaches because cybercriminals consider them to be one of the easiest entry points to attack organizations’ code bases. As supply chain attacks increase, it has become increasingly important for organizations to implement and maintain a continuous application security program and make it a priority.
Yandex Data Leak Triggers Malicious Package Publication
It would be big news, to say the least, if a large quantity of Google source code found its way into the public domain. Now imagine if the leak also included source code from Amazon and Uber. That’s the scale of the data leak that hit Russian tech giant Yandex. The risk here is that malicious actors could analyze the leaked code and discover exploitable security gaps.
Kubernetes Full Stack Recovery for Multi-Cloud Management and Disaster Recovery
Most Kubernetes users understand the complexity involved in managing multiple Kubernetes clusters, especially when those clusters are hosted in hybrid cloud or multi-cloud environments.
Cloud v/s Cloud Security - What to keep in Mind - Lalit Kumar
How to Manage Risk Effectively in Cloud-Native Environments
We’ve all got our heads in the cloud, or if not yet, we’re well on our way there. In other words, the process of digital transformation is happening at such a pace that almost all organizations will soon be working in the cloud and using cloud-native technology. Analyst Gartner has predicted that by 2025, over 95% of new digital workloads will be deployed on cloud-native platforms. This represents a 30% growth from 2021.