Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Cloud
Securing Cloud DevOps with Avishai
Cloud Native Security Fortified: Panoptica at AWS re:Invent 2023
Cloud application deployment visibility
Cloud Integrations: JFrog Achieves AWS PrivateLink Service Ready Validation
At JFrog, we talk about being universal and too integrated to fail. In addition to more than 30 technologies and package types supported natively, this also means supporting our customers in their hybrid and cloud infrastructure. One such key integration capability for customers leveraging Amazon Web Services (AWS) is AWS PrivateLink.
One Identity, AWS Directory Service Strengthen Partnership and Announce Active Roles Integration
Is Traditional EDR a Risk to Your Cloud Estate?
Organizations are transitioning into the cloud at warp speed, but cloud security tooling and training is lagging behind for the already stretched security teams. In an effort to bridge the gap from endpoint to cloud, teams are sometimes repurposing their traditional endpoint detection and response (EDR) and extended detection and response (“XDR) on their servers in a “good enough” approach.
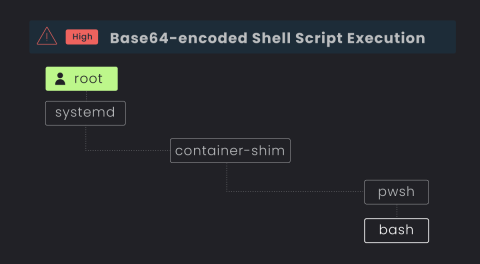
Why Traditional EDRs Fail at Server D&R in the Cloud
In the age of cloud computing, where more and more virtual hosts and servers are running some flavor of Linux distribution, attackers are continuously finding innovative ways to infiltrate cloud systems and exploit potential vulnerabilities. In fact, 91% of all malware infections were on Linux endpoints, according to a 2023 study by Elastic Security Labs.
Introducing advanced session audit capabilities in Cloudflare One
The basis of Zero Trust is defining granular controls and authorization policies per application, user, and device. Having a system with a sufficient level of granularity to do this is crucial to meet both regulatory and security requirements.
Key learnings from the State of Cloud Security study
We recently released the State of Cloud Security study, where we analyzed the security posture of thousands of organizations using AWS, Azure, and Google Cloud. In particular, we found that: In this post, we provide key recommendations based on these findings, and we explain how you can leverage Datadog Cloud Security Management (CSM) to improve your security posture.