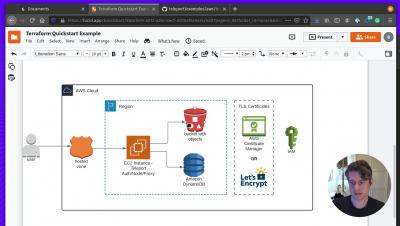
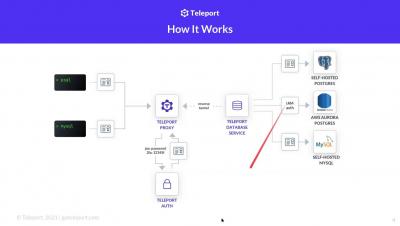
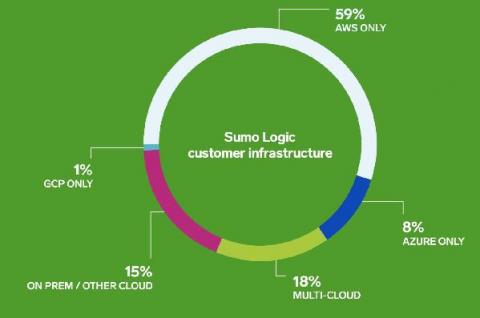
Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Cloud
Cloud and Threat Report: Shadow IT in the Cloud
The number of cloud apps being used in the enterprise increased by 20% in 2020, when the COVID-19 pandemic caused a sudden and dramatic shift to remote work for knowledge workers worldwide. Individuals, teams, and organizations all turned to cloud apps to help address some of the new challenges of remote work. The increase in the number of cloud apps was led by an increase in consumer and collaboration apps, the fasting spreading of which included Discord, Zoom, Lumin PDF, and…Xbox LIVE?
Snyk IaC scanning enhancements include Azure and AWS infrastructure as code
Recently I wrote about Infrastructure as Code (IaC) and how Snyk’s IaC scanning can help catch issues in your templates before they make it to provisioning. Our engineering team continues to expand the breadth of our IaC scanning policies to better protect your platforms from vulnerabilities and issues.
Cloud Threats Memo: Hard Times for ARM-based Mac M1 Processors
The Cloud Threats Memo is a weekly series from Paolo Passeri, digging into a recent cloud threat and highlighting how Netskope can best help mitigate it. Just a few months after their debut in November 2020, the new ARM-based Mac M1 Processors have already attracted the unwanted attention of cybercriminals with two adware samples, the details of which have been revealed over the past few days.
Understanding Cloud as an Attack Vector
In December, Netskope Threat Labs presented our work, “Cloud as an Attack Vector,” at the 23rd International AVAR Cybersecurity Conference. The Association of Antivirus Asia Researchers (AVAR) is a non-profit organization with members from 17 countries and facilitates knowledge sharing, professional development, networking, and partnering for cybersecurity experts and organizations. Ours was one of 27 presentations from 14 different countries featured at the conference.
Dangerous defaults that put your IT environment at risk: IT security under attack
In this blog in the “IT security under attack” series, we wanted to shed some light on an unfamiliar and seldom discussed topic in IT security: the default, out-of-the-box configurations in IT environments that may be putting your network and users at risk. Default settings, and why the initial configuration is not the most secure
How the COVID-19 pandemic has changed IT & Security
Modernizing Your Data Protection Strategy
Sharing data is the basis for all business processes and what drives operations and productivity. Today, more than 50% of organizations’ data is in the cloud and the typical enterprise now deploys more than 2,400 cloud applications. Concurrently, data protection remains the nexus between cloud apps, web services, and an increasingly larger number of remote users in support of modern business initiatives.
Cloud Threats Memo: Surprising Findings from Q4 2020 Phishing Trends Report
The Cloud Threats Memo is a weekly series from Paolo Passeri, digging into a recent cloud threat and highlighting how Netskope can best help mitigate it. The Anti-Phishing Working Group has recently released its Q4 Phishing Trends Report 2020, which analyzes the top phishing attacks and other identity theft techniques, as reported by the members of the group.