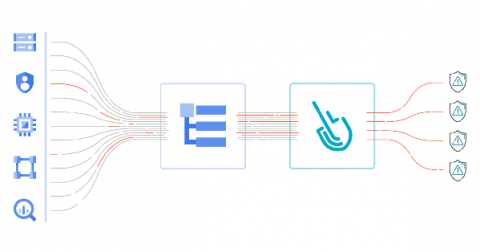
Preventing Recent Microsoft Exchange Vulnerabilities and Similar Attacks Using Netskope Private Access
On March 2, Microsoft released patches to address four zero-day vulnerabilities in Microsoft Exchange Server software. Those vulnerabilities, known collectively as ProxyLogon, affect on-premises Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019. (Exchange Online, which is part of Microsoft 365, has not been affected.)