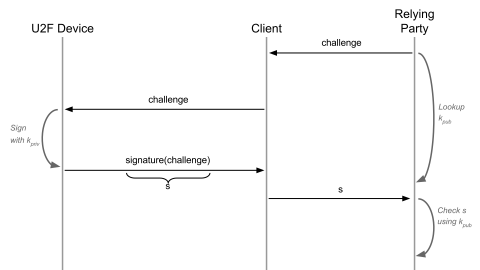
Elevate Your Cloud Security Posture with Splunk and Google Cloud
It’s more critical than ever to secure your company data and protect your workloads in the cloud. This blog post is a roundup of the latest technical resources and product capabilities by both Google Cloud and Splunk to enhance your threat prevention, detection, and response techniques, regardless of where you are in your business-transforming cloud journey.