Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Cloud
Netskope CTE and CrowdStrike Demo
The Right Steps to SASE: Refactor Internal Data Center Controls to Closed Loop Risk Management
The following is an excerpt from Netskope’s recent book Designing a SASE Architecture for Dummies. This is the sixth in a series of seven posts detailing a set of incremental steps for implementing a well-functioning SASE architecture. Throughout this series, we repeat that the data center is just one more place people and data have to go—it’s no longer the center of attention.
Is Google Drive HIPAA Compliant?
Google Drive is one of the oldest and most well known cloud storage and productivity suites. Although Google Drive launched in 2012, Google’s productivity platform dates back to 2006, when Google Docs and Google Sheets first launched. Over the years, Google would more closely integrate these services before moving them under the Google Drive and Google Suite brand. Today, Google Drive and Google’s entire suite of collaborative tools are referred to as Google Workspace.
Cloud Computing Security: A Primer
Gartner forecasts that worldwide public cloud end-user spending will grow 23% to USD 332.3 billion in 2021 as cloud technologies become mainstream. As cloud computing architectures continue to become more prevalent, “cloud native” has become a popular buzzword. But what exactly does “cloud native” mean and what impact does it have on security? How exactly do you secure all these cloud native applications?
Tagging Teleport Resources with Labels
5 Top Tips for Cloud Security from Enterprise CISOs
The Financial Times hosted an excellent event recently, at which I joined Naina Bhattacharya, CISO for Danone; Manish Chandela, Group CISO for Unipart and Florence Mottay, Global CISO for Ahold Delhaize, to discuss cloud security. The FT’s Dan Thomas moderated and the panellists all shared some excellent and candid insights into cloud threats and security strategies within their organisations.
Cloud Threats Memo: Beware of Leaky Buckets and Cloud Apps
Another memo, another leaky cloud app compromising the personal information of hundreds of thousands of individuals (and yes, you can easily guess the app that exposed the data so no spoiler alert needed—it was an S3 bucket). The latest organization to join the long list of victims of cloud misconfigurations is Cosmolog Kozmetik, a popular Turkish online retailer that exposed more than 9,500 files, totaling nearly 20 GB of data.
Teleport has been named a Cool Vendor in Gartner's Identity-First Security report
Today we are happy to announce that Teleport has been included as a Cool Vendor in Gartner Cool Vendors in Identity-First Security report. “We believe Teleport’s inclusion in the Identity-First Security Report by Gartner is confirmation that Teleport solves a huge problem of accessing cloud-native resources that traditional PAM tools did not,” said Ev Kontsevoy, co-founder and CEO of Teleport.
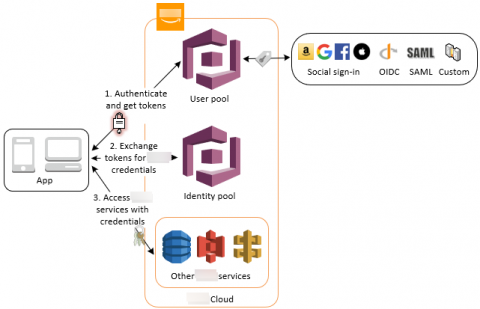
How does AWS IAM role, STS and Identity Pool work with each other.
We talked about IAM in the past 3 posts, identities in IAM, manage users privilege as an IT person and control privilege boundaries. We also talked about how applications use AWS Cognito Identity Pool to get AWS temporary credentials to access AWS resources in early posts of “What I wish I could have learned before starting using AWS Cognito” and “Authentication and authorization with AWS Amplify under the hood”.