Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Cloud
Stop Using Static Security to Protect Dynamic Clouds
Software-as-a-service (SaaS) has taken over the world because it’s easy. With just a few clicks, business units can find an application that’s suitable for a particular business process. They can subscribe to it and immediately start using it — and the IT department might never find out.
View All Your Clouds in a Single Pane of Glass
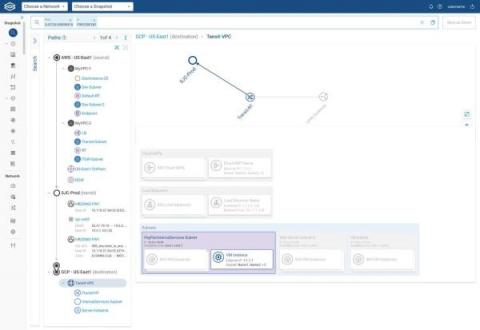
If your enterprise is like most of Forward Networks’ customers, then your IT shop oversees a sizable cloud estate. You probably have hundreds of accounts, projects, or subscriptions across different cloud vendors. There are tons of related objects too — virtual machines, firewalls, transit gateways, subnets, and more. And cloud-native apps? Maybe you hundreds of those in use or development as well.
Veracode Achieves AWS Security Competency Status
We are proud to announce that we have recently achieved AWS Security Competency Partner status. This status exemplifies our technical expertise and dedication to helping customers secure their software at every stage of cloud adoption.
How Security Service Edge (SSE) Can Help Federal, State, and Local Government Security Leaders in Their Zero Trust Journey
The federal government continues to make progress towards Zero Trust (ZT) adoption. On May 12, 2021, President Biden signed Executive Order 14028 to improve the nation’s cybersecurity and protect federal government networks and on January 26, 2022, the Office of Management and Budget (OMB) released a Federal strategy to move the U.S. Government toward a Zero Trust approach to cybersecurity.
Why is MFA important to your cloud account
Recently, we have been facing a recurring problem related to cloud security – breaches based on credentials leak or breakage. Users tend to log into their accounts using a single factor system, such as a user and password combination. This introduces a single point of failure in your account’s security. Weeks ago, we read a tweet about a person dealing with a huge AWS bill due to a stolen key that was taken by attackers to use AWS Lambda functions for crypto mining.
Securing cloud infrastructure for PCI review
The PCI certification process is quite comprehensive and relates to infrastructure, software and employee access to systems, in particular to datasets and the way that they are accessed. These checks are critical not only to the wider payments industry but also to create a level of trust with users knowing their data is protected. The PCI compliance process is a number of checks, usually by an accredited third party, to ensure that secure data handling processes are in place.
What Are the Benefits of Adopting the Cloud in Industrial Cybersecurity?
Cloud adoption has come a long way from its early days where corporate executives questioned the stewardship of their data. The initial suspicions of “where’s my data” have been laid to rest, as administrative tools and contractual obligations have emerged to give better visibility to, and accountability of, data custodianship. Even the capabilities of technology professionals have been enhanced to include full certification paths towards demonstrating cloud proficiency.
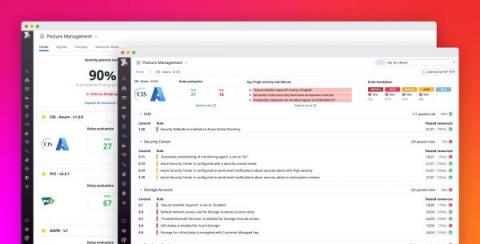
Monitor the security and compliance posture of your Azure environment with Datadog
Governance, risk, and compliance (GRC) management presents some unique challenges for organizations that deploy a myriad of cloud resources, services, and accounts. Simple misconfigurations in any of these assets can lead to a serious data breach, and compliance issues become even more prevalent as organizations try to inventory and manage assets across multiple cloud platforms and security and auditing tools.