Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
API
AWS RDS data security best practices
Amazon’s Relational Database Service (AWS RDS) allows you to offload the responsibility of managing a database, but it also comes with the risk of another external dependency. Fortunately, AWS provides some tools and settings to help with this. When you combine your existing data security policy with the AWS tooling and the advice in this article, you'll be well on your way to managing risk more effectively. Let's dive in with 15 AWS RDS data security best practices.
Rubrik and GraphQL - Episode 4 - Powershell
Rubrik and GraphQL - Episode 3 - GraphQL Mutations
Rubrik and GraphQL - Episode 2 - GraphQL Queries
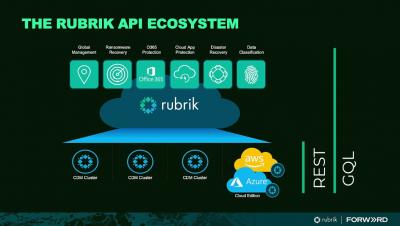
Rubrik and GraphQL - Episode 1 - REST vs GraphQL
The ultimate guide to securing data for Rails developers
Secure your apps! Protect sensitive data! Easy to say, harder to find solid answers on all the bits and pieces you need to adjust to make sure that happens. That's why we've put together this list of practical advice for securing your Ruby on Rails applications. Whether you're a Rails developer or work on any stack that relies on cloud technologies, we think you'll find something that stands out.
Data Security Controls: Six Types and How to Implement Them
According to IBM's 2021 report, the average data breach cost more than $4 million worldwide in 2021. In the United States, that number rises to $8 million. That's an over 10% increase over the previous year. So, data breaches are a significant business risk. But costs aren't the only reason to tighten your security. Breaches hurt your clients and your company's reputation. You've seen data breaches in the news. Every day brings news of a fresh attack.
Mend API Helps Make SBOMs Simple
The proliferation of third-party software components such as open source software(OSS) has triggered a growing need to keep track of it all. Why? Because when security vulnerabilities inevitably crop up in open source components, it’s pretty important to know whether your company uses that piece of code – or whether it appears in the myriad software dependencies inherent in open source.
Data Discovery: A Detailed Guide to the What, Why, and How
Modern business runs on data. Even companies that produce and sell physical products create, store, and use data. They need it to find customers, maintain relationships, sell products, and monitor costs and profits. Therefore, data is valuable. It's worth protecting, especially when you consider how often we hear about bad actors stealing it. But you can't protect something you don't know you have. You need a complete picture of what data your business is producing, storing, and using.