Solid Infrastructure Security without Slowing Down Developers
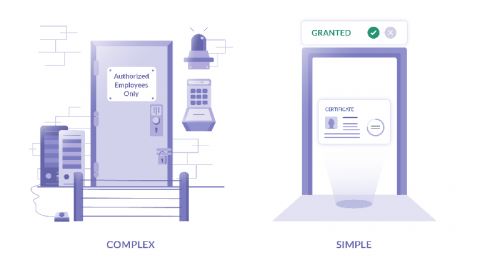
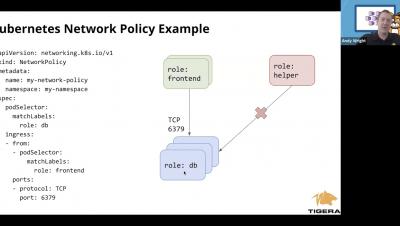
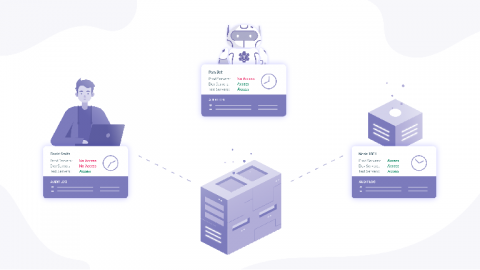
In this post, I want to share my observations of how SaaS companies approach the trade-off between having solid cloud infrastructure security and pissing off their own engineers by overdoing it. Security is annoying. Life could be much easier if security did not get in the way of getting things done.