Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Technology
The Importance Of Cloud-based Security For Businesses
How to Recover from API Downtimes and Errors
APIs are stable, until they aren’t. We talk about that often at Bearer. If you control the APIs, it gets easier, but with third-party APIs and integrations it can be more difficult to predict when an outage or incident is about to happen.
Why Blockchain Needs Kubernetes
In under five years time, Kubernetes has become the default method for deploying and managing cloud applications, a remarkably fast adoption rate for any enterprise technology. Amongst other things, Kubernetes’s power lies in its ability to map compute resources to the needs of services in the current infrastructure paradigm. But how does this tool work when faced with the new infrastructure layer that is blockchain? Can the two technologies be used in conjunction?
Gravitational Teleport: Zero Trust Access that does not get in the way.
Machine Learning APIs for Web Developers
Machine learning (ML) used to be a tool limited to specialized developers and dedicated teams. Now, thanks to many web service providers and approachable tooling, your applications can use pre-build learning models and machine learning techniques the same way you would use any web service API. This is a quick way to test out and benefit from machine learning without having to invest in artificial intelligence, building your own learning models, or shaping your application around ML.
How to find your Google or YouTube API Key
This guide explains how to get started with any Google API, such as Google Maps, Google Calendar, Youtube, or Google Sheets. Google's APIs can allow your application to integrate with Google services on the web or in a native application. There are three types of credentials for Google APIs.
Sumo Logic and NIST team up to secure energy sector IoT
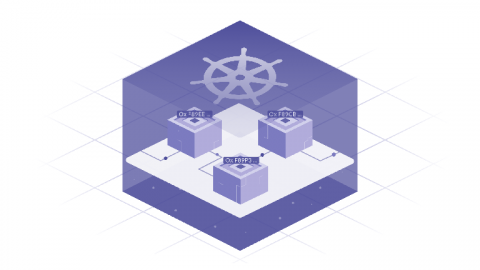
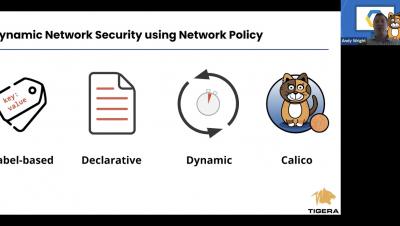
How to Implement Network Policy in Google GKE to Secure Your Cluster
Remote workers making mobile management and security first priority
In recent years, many businesses had already begun planning for a gradual shift towards an increasingly remote workforce, yet fewer had implemented a mobile-first strategy, and some were still formulating strategies. At a gradual pace, IT administrators could handle a small percentage of remote workers and saw the management features of device enrollment programs and network security measures as enough to manage a few remote devices and cyber risks.