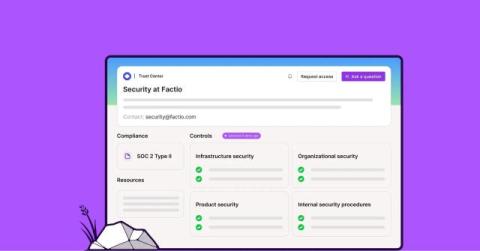
Building a comprehensive Trust Center
In today's digital landscape, trust is paramount. Customers want to know that their data is secure and that they can rely on the companies they do business with. One of the best ways to provide this assurance is through a well-crafted, up-to-date Trust Center. But what exactly should go into a Trust Center? How easy are they to maintain, and how much manual work do they save security teams?