Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Stories from the SOC - Propagating malware
While freeware does not have monetary cost, it may come at a price. There may be limitations to freeware such as infrequent updates, limited support and hidden malicious software. Some freeware programs may have added software packages that can include malicious software such as trojans, spyware, or adware. It’s important to have additional layers of defense to provide that your environment is protected.
XR Money Rebellion Planning Movement Vs Banks, Financial Institutions
Extinction Rebellion (XR) is a London-based environmental group aiming at disruptive and nonviolent civil resistance. Launching their first public campaign in October 2018, XR centers their motives on resisting structures that dismiss climate change and degradation of natural resources[1]. XR has been notable in eliciting mass arrest, a Ghandian tactic that garnered them press coverage, funding, and attention from government agencies and policy bodies.
10 tips to improve small business cyber security
Top 5 Most Powerful IoT Security Testing Tools
The network of interconnecting devices to exchange data popularly known as the Internet of Things is evolving rapidly in the fast-paced industry of technology. However, advancement in IoT has also taken a toll on security. IoT Systems strive to enhance productivity, efficiency, and flexibility but also invite uncalled risks to the network. IoT Security stands as the need of the hour for secure and holistic development.
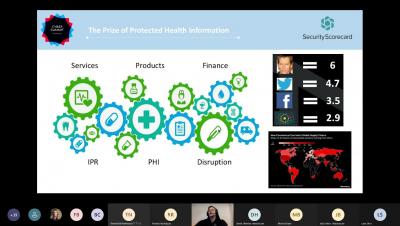
Third-Party Risk Management in Healthcare
Hangin' with Haig: Conversations Beyond the Keyboard with Guest Simon Jones of Helping Rhinos
Cloud Threats Memo: Keeping Sensitive Data Safe From Personal Instances
Cloud-native threats have multiple implications. We are used to seeing legitimate cloud applications exploited within sophisticated kill chains, and we forget the basics: such as the risks posed by Shadow IT, like when personal email accounts are used to improperly handle corporate data. This is a very real risk right now, when users are working almost completely from home and the line between the professional and personal use of work devices is blurred.
Overview: CyberResearch by UpGuard
UpGuard has launched an exciting new product called CyberResearch. This post summarizes the solution and its key features. CyberResearch is a suite of fully managed services, encompassing third-party risk and data leak detection. This world-first innovation is designed to further reduce the risk of data breaches while making it easier than ever before to scale your cybersecurity efforts.