Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Data Subject Access Request: Article 15 GDPR - The Right of Access
In today’s data-driven world, every other company and application collects a significant amount of important data and individual’s personal information such as name, email ID, address, date of birth, ID number, credit card information, and online behaviours, history and much more. Sharing data has become an essential component to many businesses and organisations; it allows the data controller and data subjects to stay connected and collaborate on many things.
The top 10 network security vulnerabilities for businesses in 2021
As per UK DCMS’s data breaches survey, about 32% of businesses in the UK have faced a form of cybersecurity threat between 2018 and 2019. As a result of these network security vulnerabilities, these businesses incurred costs on lost data and many other damages that totalled £4,180.
Cybersecurity and Compliance for Healthcare Organizations
Amidst the pandemic overwhelming the capacity of many hospital systems, malicious hackers have been quick to target healthcare providers and medical agencies. These cyber-attacks have hit both the United States and Europe in recent months, serving as a reminder for organizations to closely review their information security posture during these times of uncertainty.
NAME:WRECK DNS Bugs: What You Need to Know
For most internet users, there’s not much of a perceivable difference between the domain name they want to visit and the server that the domain queries. That’s because the Domain Name System (DNS) protocol does a good job of seamlessly routing users to different IP addresses that are all associated with a single domain name.
Bulletproof
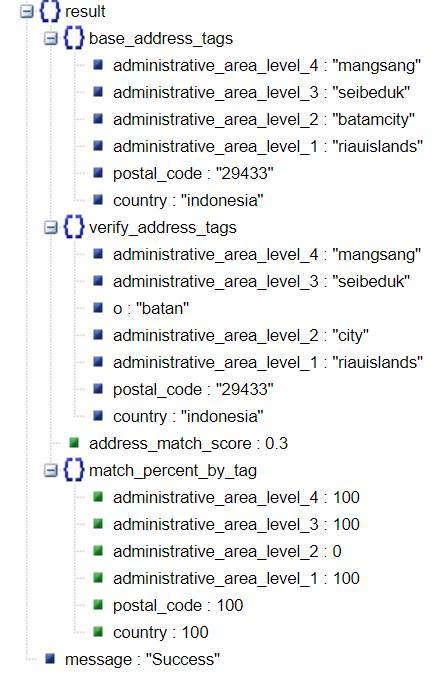
Product Update: Address Net Model for Address Verification
Complex address systems and its verification have continued to be a big riddle for technology companies. Currently address verification is done manually by matching the address mentioned in the identity document with the address filled in any kind of application form filled by the customer.
SuiteCRM: PHAR deserialization vulnerability to code execution
SuiteCRM is a free and open source Customer Relationship Management application for servers. This advisory details a PHAR deserialization vulnerability that exists in SuiteCRM which could be leveraged by an authenticated administrator to execute commands on the underlying operating system. This issue has been fixed in release 7.11.19. In PHP, PHAR (PHP Archive) files can be used to package PHP applications and PHP libraries into one archive file.
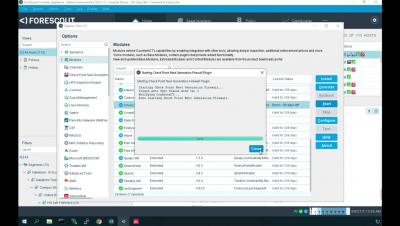
How To: Orchestrate Check Point NGFW with eyeExtend
Weekly Cyber Security News 07/05/2021
A selection of this week’s more interesting vulnerability disclosures and cyber security news. For a daily selection see our twitter feed at #ionCube24. With images of all the best spy movies out there, you just can’t help enjoy this one. While its not possible to control the driving of the car, flinging the car doors open at speed might have an interesting effect on the occupants (and allow our spy to gain access of course while swinging from the drone).