Preventing Data Breaches in User-Developed AI Applications on Low-Code Platforms
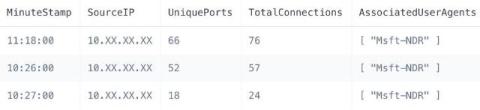
As more and more companies adopt low-code platforms and launch AI applications, the need for proper data security has never been greater. While it’s true that low-code platforms give users the freedom to develop powerful AI solutions with minimal programming knowledge or experience, this same level of flexibility also inadvertently exposes applications to potential data breaches.