Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Ask SME Anything: What's the difference between a Web Filter, a SWG, and a Next Gen SWG?
The Zero-Trust Journey in 5 Phases
For a concept that represents absence, zero trust is absolutely everywhere. Companies that have explored how to embark upon zero-trust projects encounter daunting challenges and lose sight of the outcomes a zero-trust approach intends to achieve. Effective zero-trust projects aim to replace implicit trust with explicit, continuously adaptive trust across users, devices, networks, applications, and data to increase confidence across the business.
DevOps Access Controls for CI/CD, GitOps, and More
Over the last few years, the term DevOps and DevSecOps (which stand for Developer Operations and Developer Security Operations respectively) have become synonymous with companies trying to become more agile and less monolithic.
What is Endpoint Detection and Response (EDR)?
It can take just minutes, if not seconds, for an advanced threat to compromise a company's endpoint devices (laptops, mobile devices, and the like). Legacy security tools that were once adored and worshipped by many no longer cut it. These tools require manual triage and responses that are not only too slow for fast-moving and increasingly sophisticated cyber threats, but they also generate a huge volume of indicators that burden the already overstretched cyber security teams.
Expanded Suricata detections with Dtection.io
One of the most common questions that Corelight customers and prospects who are using our Suricata integration ask is “what signatures should I run?” While our answer has always started with the industry-standard Emerging Threats Pro feed, we recognize that other feeds - like the ones from Crowdstrike or private industry groups - often make excellent additions to the ET Pro set.
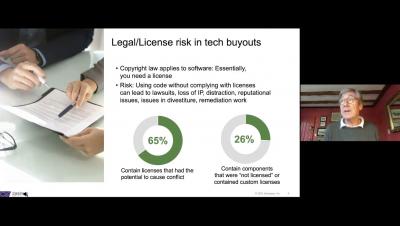
Software risks in private equity buyouts | Synopsys
Using Veracode From the Command Line in Cloud9 IDE
Hello, Clint Pollock, principal solutions architect here to explain how to use Veracode completely from a command prompt in your IDE or CI/CD system. I’m going to teach you how to submit a static policy scan and a static sandbox scan. Then, I’m going to clean up some builds using the API, submit a static pipeline scan, a software composition analysis scan, and a dynamic scan … all from the command prompt. Let's get started!
Elastic Security Overview
"PlugWalkJoe" indicted for $784K SIM swap cryptocurrency theft
The U.S. Department of Justice charged a British man for his alleged role in stealing $784,000 worth of cryptocurrency using SIM swap attacks. According to the unsealed indictment, Joseph James O’Connor – also known as “PlugWalkJoe” – conspired with others to steal approximately $784,000 worth of cryptocurrency from a Manhattan-based cryptocurrency company.