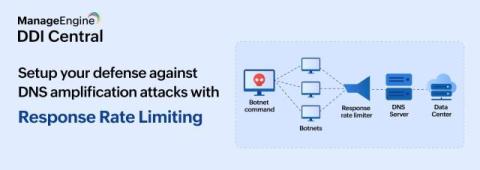
What is response rate limiting? How does it help in securing your critical network infrastructure?
Organizations often face different forms of cyberthreats and cyberattacks, and attackers try to get their hands on confidential data which would result in major loss of reputation, customer’s information, etc. So, organizations should implement networking tools to secure their data.