Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Network Security for D2iQ Konvoy
GDPR Turns Two: What We've Learned So Far
Around 9 Million easyJet Customers' Details Stolen in Hacking Incident
British low-cost airline group easyJet revealed that an hacking incident had exposed approximately nine million customers’ information.
Winning with Cyber Threat Intelligence: Taking a More Personal View
In this final article of our trilogy, we investigate how a cyber threat intelligence (CTI) analyst and associated programmes provide insight about physical and cyber threats to your organisation. The value of these insights is reflected in the wins, which come as a result of context building, holistic understanding, and enhanced awareness in order to outmanoeuvre malicious actor(s).
Attacks Targeting ICS & OT Assets Grew 2000% Since 2018, Report Reveals
The digital threat landscape is always changing. This year is an excellent (albeit extreme) example. With the help of Dimensional Research, Tripwire found out that 58% of IT security professionals were more concerned about the security of their employees’ home networks than they were before the outbreak of coronavirus 2019 (COVID-19).
Locked Down But Not Locked Out: Business As Usual with Lawton Communications Group
It’s one thing to simulate your disaster recovery and business continuity response; it’s quite another to have to stress test your plan for real and at scale. Recently we chatted with Norman Cave-Browne-Cave, IT & Facilities Manager at Lawton Communications Group, the guy in the hot seat when the lockdown came. The task fell to Norman to maintain business as usual for his team in the UK, US and Australia. Here, he reflects on his experiences.
Machine Learning APIs for Web Developers
Machine learning (ML) used to be a tool limited to specialized developers and dedicated teams. Now, thanks to many web service providers and approachable tooling, your applications can use pre-build learning models and machine learning techniques the same way you would use any web service API. This is a quick way to test out and benefit from machine learning without having to invest in artificial intelligence, building your own learning models, or shaping your application around ML.
Derbyshire Fire & Rescue Service: Fighting cybersecurity fires with Splunk
Everyone at Splunk is very proud of the amazing things that our customers and partners do with their data. It is always extra special when one of those organisations is really doing good and looking after us all in our daily lives. I’m delighted to share one of those stories from the Derbyshire Fire & Rescue Service (DFRS) who is using Splunk as its data-driven SIEM.
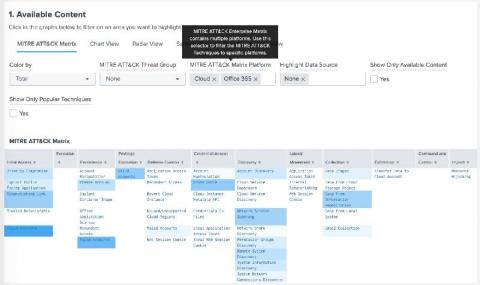
Splunk Security Essentials 3.1: Enhanced MITRE ATT&CK Matrix: Find the Content that Matters the Most to You, Faster
One of the great things about developing for Splunk Security Essentials is that most of the features and capabilities are requested from customers and the security community. In this latest release (3.1), we added a feature that has been requested frequently: the ability to filter the ATT&CK Matrix for Cloud and SaaS Techniques. The MITRE ATT&CK Framework consists of multiple matrices such as Enterprise, Mobile, and ICS.