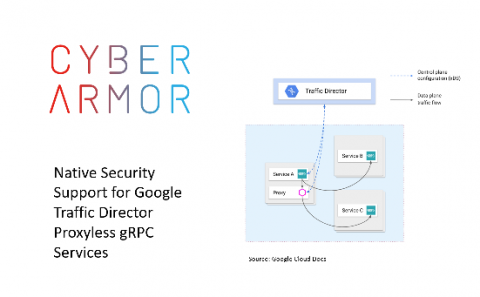
Cyber Armor for Google Traffic Director gRPC Proxyless Services
In its latest announcement of Traffic Director’s support for gRPC Proxyless services in service mesh Google addresses the well-known (yet less spoken of) trade offs for using sidecars to handle networking on behalf of your applications.