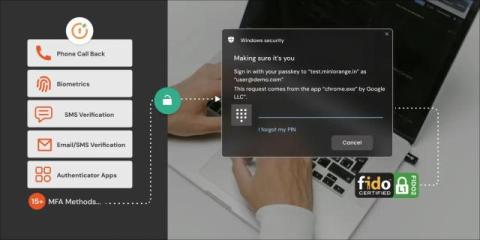
How Cybersecurity Risk Assessments Will Need to Evolve for 2025
2025 is drawing near, and the cybersecurity scene is changing quickly. Organizations must adapt how they undertake cybersecurity risk assessments in tandem with the ongoing evolution of technology and the escalating sophistication of cyber-attacks. In order to address the difficulties of the near future, cybersecurity risk assessments will need to change in ten key areas, as this essay examines.