Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
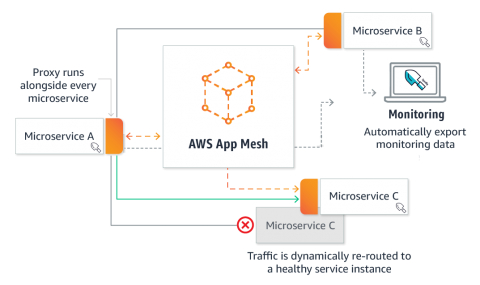
Providing Visibility and Security for AWS App Mesh
Microservice architectures running on containers have made applications easier to scale and faster to develop. As a result, enterprises are able to innovate faster and accelerate time-to-market for new features. To make management of microservices even more efficient and easier to run, service mesh solutions like Istio, Envoy, and Linkerd – and now AWS App Mesh – have become the next core building blocks of microservices infrastructure built on containers.
How to Improve Compliance in a Company
Highly regulated financial institutions often struggle with compliance management. As a financial institution matures its cybersecurity compliance program, the document management requirements often mean they need to find automated solutions that can create a single source of truth to ease audit stress.
Rethinking Security in the Age of DevSecOps
Security Requires Immutability: Avoid Dynamic Environments with Change Management
When Shelley published his famous poem in 1816, he was telling us that the only constant in life is change. This was not a new concept, even then. Heraclitus proposed the same concept around 500 BCE with ‘Panta rhei’ (Life is Flux or everything changes). Even though we all know and understand this ancient concept, people still have difficulty with change.
3 Reasons Log Management is Critical for Business Intelligence
Log management is the answer to all of your digital transformation woes. No, hear me out. At its heart, log management is the (challenging) task of collecting and storing all machine-generated data from across your entire enterprise into a common repository. If this collection doesn’t happen, or if log collection is limited to certain datasets, there’s little chance of deriving those high value insights you dream of.
What You Should Know About Ransomware in 2019
It’s estimated that Ransomware costs will climb to roughly $11.5 billion in 2019, according to CSO Online. The frequency of attacks continues to increase as well. According to a report on Ransomware, these attacks occurred once every 120 seconds in early 2016. By 2017 this spiked to an attack occurring every 40 seconds. In 2019, the frequency is expected to grow to an attack happening every 14 seconds.
Container compliance for Docker and Kubernetes
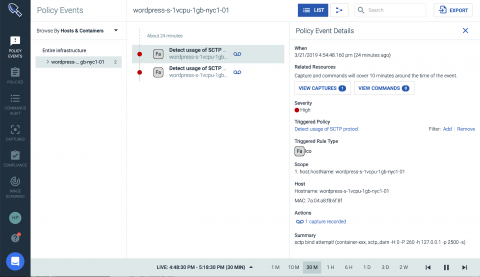
Detecting and preventing cgroups escape via SCTP - CVE-2019-3874
This week CVE-2019-3874 was discovered which details a flaw in the Linux kernel where an attacker can circumvent cgroup memory isolation using the SCTP socket buffer. In containerised environments, this has the potential for a container running as root to create a DoS.
Weekly Cyber Security News 22/03/2019
A selection of this week’s more interesting vulnerability disclosures and cyber security news. A news busy week this has been, from a catastrophic malware hit against an global manufacturer to startling breaches from the usual players. Which to pick out then? OK, a wonderful article by Krebs that caught my attention today.