Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
How to Get Started in Digital Forensics
If you want to become a digital forensic expert, be aware that when entering the field, you will be presented with an abundance of information that you will not know. It is a wonderfully challenging career path. Some believe that having the title of a cybersecurity professional (e.g. digital forensics expert, cybersecurity analyst, incident response commander, etc.) means that this is an area where the field of knowledge is intimidating because it’s so expansive.
NetOps vs DevOps vs DevSecOps - What's the Difference?
One thing I have noticed is that each industry comes up with their own terms and acronyms. Unfortunately, these inventions often vary depending on the person you speak to due to a lack of a governing body that decides on an exact definition. At times, acronyms can even overlap, causing further confusion. Therefore, when it comes to definitions, I always look to ask a variety of persons from across industries on how they would define certain terms.
Weekly Cyber Security News 21/02/2020
A selection of this week’s more interesting vulnerability disclosures and cyber security news. For a daily selection see our twitter feed at #ionCube24. Extortion methods have been pretty consistent the past couple of years, but a new one popped up this week which seems to be focused on the online small business owner. I wonder how this one will pan out.
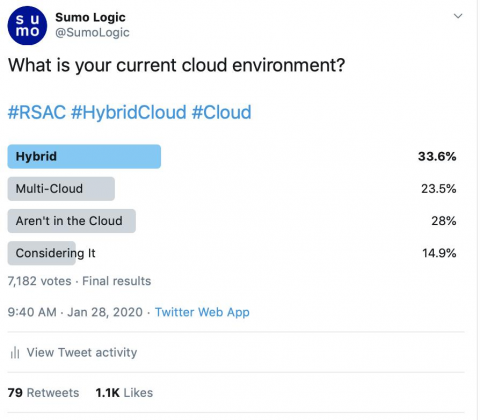
Pre-RSA Twitter Poll: 3 Interesting Observations on SOC, SIEM and Cloud
What is DLP?
What is the value of ethical hacking for businesses and society?
Mainstream media coverage of hacking often perpetuates the stereotype of hoodie-wearing hackers up to no good. For this reason, some people remain sceptical about hacking, even if it is in relation to ethical hacking undertaken by cyber security professionals.
Workforce Management Software
Workforce management, often shortened to simply WFM, is about managing staff schedules and services within companies. Workforce management software incorporates most software that focuses on managing and simplifying the process of scheduling staff work hours as well as managing their work and productivity. Managing large amounts of staff members turns into a massive task for human resources teams if they have to do everything manually.
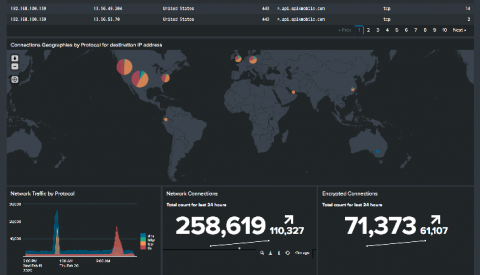
The Power of Splunk Security Essentials + Accedian Skylight Powered Security
As new technologies emerge, end-to-end application stacks continue to grow, and connected devices become more omnipresent in everyday lives, our society will only become more intrinsically connected across multiple touchpoints. It’s even estimated that in the US alone, there will be roughly 200 billion IoT devices by the end of 2020.
Is the cybersecurity skills gap real?
An independent guest blogger wrote this blog. If you do a web search for “cybersecurity skills gap,” you’ll get many, many pages of results. It’s certainly a hot topic in our industry. And it’s a matter that security practitioners and human resources people often disagree on. But before I get further into the matter, it would help to know what it is we’re talking about when we use the phrase “cybersecurity skills gap.”