Importance of Securing and Simplifying DNS Infrastructure
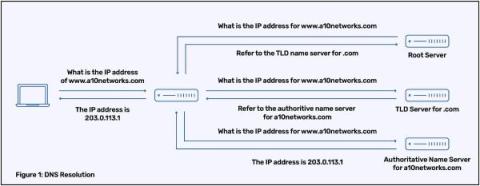
Domain Name System (DNS), informally referred to as the “phonebook of the internet,” is one of the mainstay protocols that makes the internet work by translating reader-friendly domain names into IP addresses and vice-versa.