JFrog4JFrog: DevSecOps Made Simple
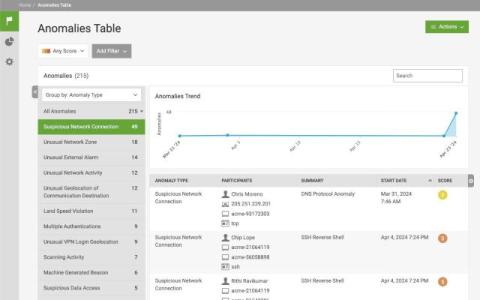
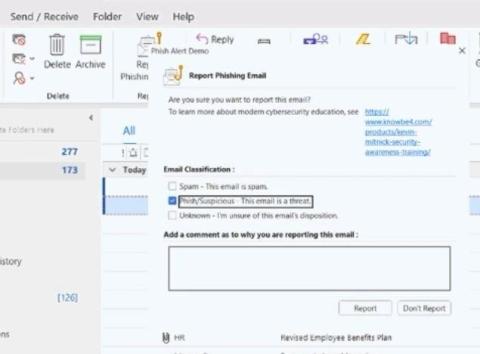
Developers simply want to write code without interruption, while operations wish to build as fast as possible and deploy without restrictions. On the other hand, security professionals want to protect every step of the software supply chain from any potential security threats and vulnerabilities. In software development, every piece of code can potentially introduce vulnerabilities into the software supply chain.