Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Enabling Secure Kubernetes Multi-Tenancy with Calico Enterprise
State of Software Security v11: The Most Common Security Flaws in Apps
For our annual State of Software Security report, we always look at the most common types of security flaws found in applications. It’s important to look at the various types of flaws present in applications so that application security (AppSec) teams can make decisions about how to address and fix flaws. For example, high-severity flaws, like those listed in OWASP Top 10 or SANS 25, or highly prevalent flaws can be detrimental to an application.
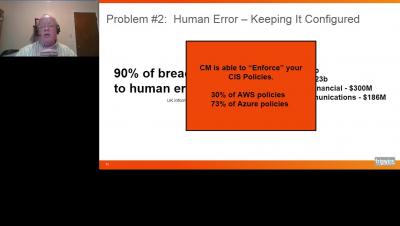
Secure Your Journey to the Cloud with Tripwire Configuration Manager
Survey: 78% of Retailers Took Additional Security Precautions Ahead of the 2020 Holidays
Coronavirus 2019 (COVID-19) stopped many things in 2020. While in-store holiday shopping may be greatly reduced for some, there’s still a lot of shopping happening online. Near the end of November 2020, Statista revealed that holiday retail sales were expected to grow approximately 3.6% over the previous year. And Adobe Analytics reported that online sales would likely rise 33% to a record $189 billion.
From a Single Pane of Glass, to Functional Dashboards to Manage Cyber Risk
For the longest time, or as far as I can remember, the holy grail of all networking platforms has been the need for a single pane of glass, that single source of all information that you would need to be most effective. So, what is a single pane of glass?
Fix now: Vulnerabilities targeting the FireEye Breach
On Tuesday 8th December in an unprecedented move leading cybersecurity provider FireEye admitted they had been breached and several of their red team tools and scripts had been stolen. In this blog we look at the list of vulnerabilities in these tools and how to protect your organization.
Better Together: Egnyte's Construction Integrations
Construction, like any industry, relies on software throughout all phases of a project. From inception to completion, a plethora of programs come into play to facilitate each task at hand. The unfortunate part of having so many applications working side by side is that they treat the data the same way – side by side, in their own silos. Very often, data produced by these applications moves and morphs into the next phase – a bid becoming the basis for a contract, for example.
Why Third-Party Risk on Google Drive Should Be a #1 Concern
Sharing Google Workspace files with clients and partners feels like a normal part of doing business – especially as so many companies move to remote work. However, each time you share a file with someone outside of your organization, you increase what’s known as third-party risk. Third-party risk can open your business up to all types of internet security breaches, including IP theft, phishing attacks, malware, and data exfiltration.
Elastic Security provides free and open protections for SUNBURST
On December 13, SolarWinds released a security advisory regarding a successful supply-chain attack on the Orion management platform. The attack affects Orion versions 2019.4 HF 5 through 2020.2.1, software products released between March and June of 2020. Likewise, on December 13, FireEye released information about a global campaign involving SolarWinds supply-chain compromise that affected some versions of Orion software.