Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Falco in the open
One of the most successful aspects of Kubernetes is how functional the open source community was able to operate. Kubernetes broke itself down in smaller sections called special interest groups, that operate similarly to subsections of the kernel. Each group is responsible for a single domain, and sets their own pace. One of the most important things to a Kubernetes SIG, is the residual SIG calls.
What is an Insider Threat?
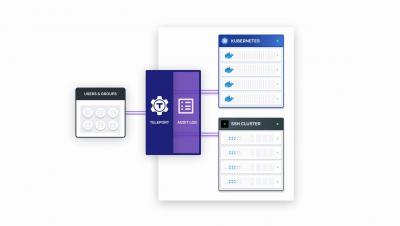
Gravitational Teleport v3.0 Demo
Gravity Overview
Disruption: The True Cost of an Industrial Cyber Security Incident
Industrial control systems are essential to the smooth operation of various national critical infrastructure. While once segmented from the web, these systems are now becoming increasingly more networked and remotely accessible as organizations transform to meet the digital age. This development potentially exposes industrial control systems to digital threats.
It's Time for a Better Workflow: Devo and Demisto Edition
Security Operations Centers (SOCs) are known as the “nerve center” of enterprise cybersecurity programs; others view them as “war rooms” or “situation rooms.” Regardless of the moniker, one thing is clear: their function is viewed as a critical competency.
Five Ways AI is Cutting Costs in Start-Ups and Small Businesses
Companies of various sizes have embraced the concept of the lean startup. Organizations are continually looking for ways to save money and stretch limited budgets to the max. Thanks to the growth in diverse applications of artificial intelligence, technology is helping companies achieve this goal.
Canada's Recommendations for Upholding Digital Security in the Financial Sector
On 29 July 2019, Capital One disclosed a digital security incident in which an outside individual gained unauthorized access to its systems. That party then leveraged their access to obtain the personal and financial information of Capital One cardholders as well as of individuals who at one point applied for a credit card. Overall, the bank holding company estimated that the breach affected 100 million Americans as well as six million Canadians.