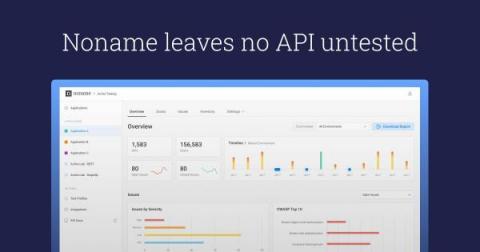
Leaving no API untested.
Today we announced the general availability of Active Testing V2, our flagship API security testing solution, and an integral part of the Noname API Security Platform. The more API security defects we can catch during development, the cheaper and more efficient our applications become. So-called shifting left has a profound effect on security if done right. Over 85% of defects, including security issues, are created in development, mainly during the initial coding phase.