How API Security Factors into DORA Compliance
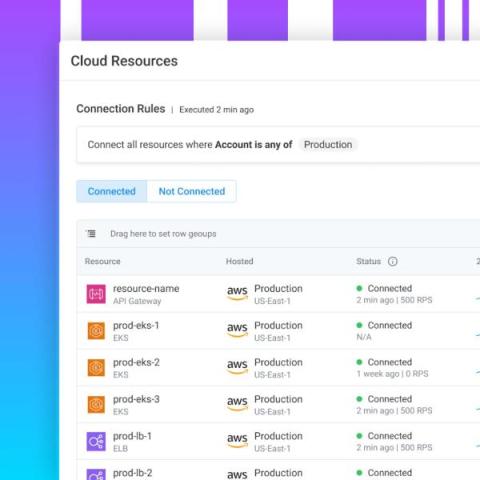
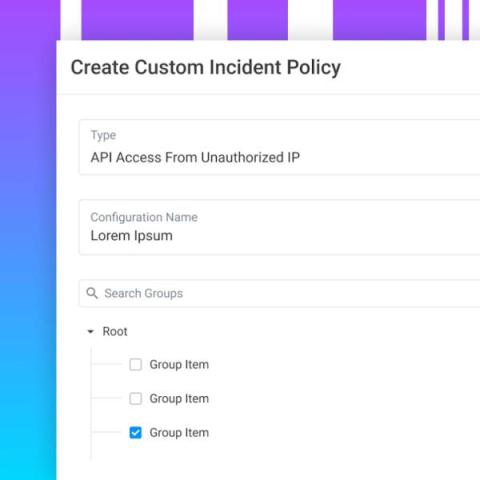
Complying with data protection regulations isn’t easy, but it has traditionally involved dealing with familiar risks. For example, do your IT admins have the right amount of access to systems touching sensitive information? Review, remediate, report, and repeat. Compliance has been cumbersome, but workable. The problem is, today’s attack surface is nowhere near workable. And it’s evolving to include threats that most compliance programs aren’t yet accounting for.