Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
3 Emerging Innovations in Technology that Will Impact Cyber Security
The war between security experts charged with the responsibility of protecting information and cyber-criminals who threaten to compromise the integrity of data for different entities has become a cat and mouse game. For instance, as soon as white hats counter one form of malicious behavior using encryption tools, there is the almost immediate development of yet another malevolent form of threat for information systems.
20 CIS Controls: Control 18 - Application Software Security
Today, I will be going over Control 18 from version 7 of the top 20 CIS Controls – Application Software Security. I will go through the eleven requirements and offer my thoughts on what I’ve found.
Internet of Things security practices for your business
Wearables, smart speakers, remote security systems, connected cars, inventory trackers, smart headphones: these are just a handful of the connected devices in modern workplaces. The Internet of Things (IoT), or internet-enabled devices that collect and act upon data, is becoming more popular with ever-increasing applications. Far beyond a smart coffee pot that automatically gets the brew going to start the workday, the Internet of Things is changing business security and vulnerability in a big way.
20 CIS Controls: Control 19 - Incident Response and Management
Today, I will be going over Control 19 from version 7 of the top 20 CIS Controls – Incident Response and Management. I will go through the eight requirements and offer my thoughts on what I’ve found.
Egnyte Expands Footprint in Healthcare & Life Sciences
Creating HIPAA compliant collaboration and management solutions for 1000+ organizations in the space
20 CIS Controls: Control 20 - Penetration Tests and Red Team Exercises
Today, I will be going over Control 20 from version 7 of the top 20 CIS Controls – Penetration Tests and Red Team Exercises. I will go through the eight requirements and offer my thoughts on what I’ve found.
7 Steps to GDPR Compliance
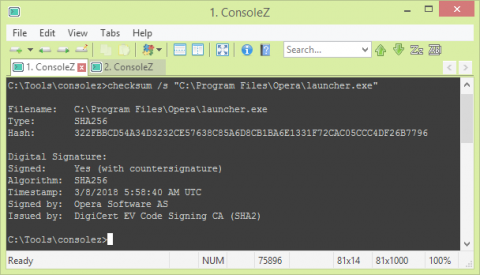
EventSentry SysAdmin Tools: Digital Signature Verification with checksum.exe
Windows supports a code-signing feature called Authenticode, which allows a software publisher to digitally sign executable files (e.g. .exe, .msi, …) so that users can verify their autenticity. The digital signature of a file can be viewed in the file properties in Windows explorer on the “Digital Signature” tab.
5 employee cyber security training questions you need to ask
Chances are your organization already addresses cyber security to some extent in new employee onboarding. Whether that’s traditional training videos on cyber security that employees watch on their own time, presentations by IT, or brochures, most employees know that their companies have cyber security protocol and best practices. But how many of your employees actually know what the protocol and practices are?