Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Splunk
Coffee Talk with SURGe: 2022-AUG-10 Live from Black Hat:
Using Threat Intelligence To Advance Your Security Posture
People often ask me, “What’s the purpose of cybersecurity?” I tell them that it serves to protect the valuable, intangible data assets of firms or private individuals, usually by trying to shrink the attack surface. One way to achieve cybersecurity is to utilize threat intelligence research in your firm’s security plan. In this article, I will discuss the benefits of understanding and implementing a threat intelligence program.
Cyberattacks in 2022: Beware These 5 Attack Types
Cyberattacks are constantly changing. That you know. But how are they changing? And which types of threats are the most prominent today? Those are the real questions you need to answer to stay ahead of modern security risks. Keep reading for a primer on the most prevalent types of cyber security threats in 2022, along with insights on how to build a defense strategy against them. (For a comprehensive view, check out our cybersecurity threats explainer.)
Splunk Announces Participation in the Open Cybersecurity Schema Framework (OCSF) Project
There’s a myth from antiquity known as the Tower of Babel, where people were working together to build a tower to the heavens, only to lose the ability to communicate with one another via divine intervention. Essentially, the groups began speaking their own languages and were unable to complete the tower. So, why are we talking about myths in a cybersecurity blog?
The Democratization of Data: The Pros & Cons of All That Data
Try going one day without navigating today’s data landscape — accepting or declining cookie pop-ups, determining whether and how a company can use your information, and all the data you’re generating simply by browsing the web. Yes, we live in the Data Age. We know we generate mind-boggling amounts of data. The data we generate in a single day is an unfathomable amount (2.5 quintillion bytes if you can do that math). More formally, we say that data has been democratized.
Security Made Stronger with Splunk User Behavior Analytics (UBA) Version 5.1
The Summer of Security continues! Hot on the heels of security announcements at.conf22 and a brand new Splunk Security Essentials 3.6.0, we’re excited to announce the availability of User Behavior Analytics (UBA) version 5.1.
The Convergence of Security and Observability: Top 5 Platform Principles
With the advances in technology and an unpredictable macro environment, IT professionals have to deal with a deluge of data, increasing cyberthreats, distributed infrastructure and workforce, a mix of modern and monolithic apps and hybrid environments. Although there is significant momentum towards the Cloud, many organizations cannot move all of their data to the public cloud due to security, compliance or technical constraints.
ML Detection of Risky Command Exploit
As described in Splunk Vulnerability Disclosure SVD-2022-0624, there is a list of SPL (Search Processing Language) commands that are classified as risky. This is because incorrect use of these risky commands may lead to a security breach or data loss. As a precautionary measure, the Splunk Search app pops up a dialog, alerting users before executing these commands whenever these commands are called.
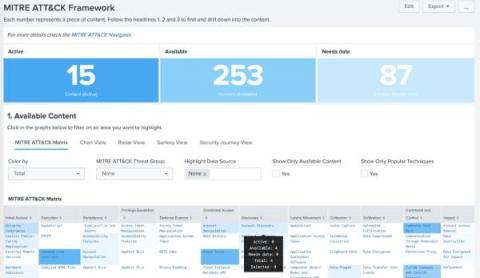
Splunk Security Essentials 3.6.0: A Holistic View of Your Security
We hope that you had a blast at.conf22 whether you attended in-person or virtually! To keep the good vibes of.conf rolling, we are releasing Splunk Security Essentials 3.6.0. For those new here, Splunk Security Essentials (SSE) is a fully supported app that is available to install from Splunkbase. There is so much to be excited about in this update and we can’t wait for you to make the most of all the new benefits.