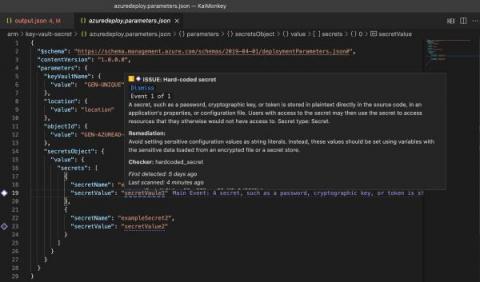
OWASP Top 10: Broken access control
Listed as #1 on the OWASP Top 10 list, broken access control is when an attacker can gain unauthorized access to restricted information or systems. Access control ensures that people can only gain access to things they’re supposed to have access to. When access control is broken, an attacker can obtain unauthorized access to information or systems that can put an organization at risk of a data breach or system compromise.