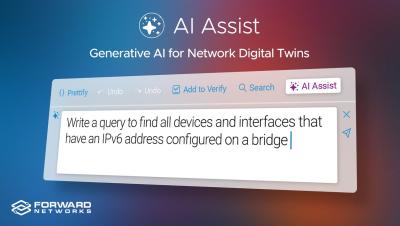
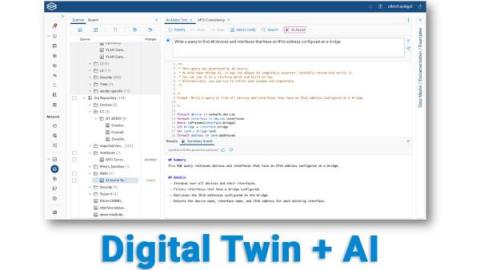
Demo Tuesday: AI Assist
If you could ask your network one question, what would it be? Good news, you can ask it all the questions you want with Forward Enterprise's new AI Assist feature. Watch Mike Lossmann use natural language to perform Network Query Engine searches-- no matter your role or skill level, you can conduct sophisticated network queries with a minimal learning curve.