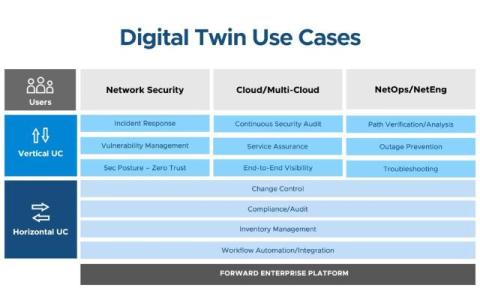
Is it Possible to See a Full Cloud Inventory in a Single View?
Join networking professionals Mike Lossman and Chris Naish as they discuss how to efficiently manage cloud inventory across AWS, Azure, and GCP cloud platforms using Forward Networks. Keeping tabs on cloud environments can be an arduous process requiring engineers to log into each cloud to gather inventory data. Chris shows how to create a centralized dashboard with Forward Networks, aggregating and filtering information from all three clouds, allowing users to view data like compute instances, VPCs, and subnets in a single location.