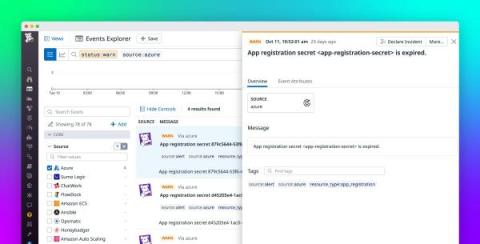
Monitor expiration events from Azure Key Vault
For customers using Azure Key Vault—which helps them safeguard sensitive keys and secrets used by applications and services hosted on Azure—it can be challenging to determine when the resources in their Key Vault(s) are about to expire. Invalid keys and secrets can disrupt your day-to-day workflows by causing application downtime, holding up incident investigations, invalidating compliance, slowing down the development of new features, and more.