Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
The Expert's Guide on Tackling the Cybersecurity Skills Gap
The skills gap is weighing heavily on the minds of digital security team members. In a survey of 342 security professionals, Tripwire found that 83% of infosec personnel felt more overworked in 2020 than they did a year earlier. An even greater percentage (85%) stated that it had become more difficult for their organizations to hire skilled security professionals since then.
MITRE Releases an Update to The Common Weakness Enumeration (CWE)
MITRE has been doing exceptional work in advancing cybersecurity as a public good, and it is an excellent resource for security professionals. Possibly best known for their ATT&CK Framework, a rich source of adversarial tactics and techniques and their mitigations, MITRE is also known for another resource: the Common Weakness Enumeration (CWE). The CWE is a community initiative sponsored by the Cybersecurity and Infrastructure Security Agency (CISA).
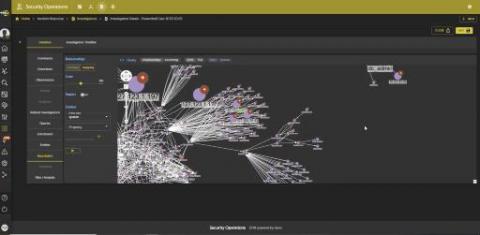
Elastic SIEM detections
With the release of Elastic Security 7.6, we've announced our creation of a modern detection engine that provides SOC teams with a unified SIEM rule experience through Elastic SIEM detections. The detection engine draws from a purpose-built set of Elasticsearch analytics engines and runs on a new distributed execution platform in Kibana.
Capitalize on Analyst Intuition for More Effective Cybersecurity
You’ve probably heard by now that we face a severe shortage of cybersecurity professionals with the skills and experience necessary to effectively defend against today’s—and tomorrow’s—threats. Cybersecurity Ventures estimates there will be 3.5 million unfilled jobs globally by 2021. Fortunately, there are key areas of the SOC workflow that can be automated to take advantage of security analyst intuition and act as a force multiplier.
5 Things a Hacker Doesn't Want You to Know
Indonesia's identity theft problem, and ways to overcome it
Indonesia is amidst a digital transformation stage, with many digital businesses booming, especially in the finance sector. However, these efforts are being hindered by a rampant identity theft problem that the nation is facing.
Deploying Applications to a Kubernetes Cluster to Which You Don't Have Access
For the impatient, in this blog post, we’ll look into the problem of preparing a Kubernetes application to be deployed into a large number of Kubernetes clusters, even if you, the developer, do not have direct access to them all. The tutorial parts of this post will utilize Gravity 7.0, which you can download here. This version is in beta at the time of publication, so be sure to select pre-releases in the dropdown on the download page to access it.
11 of the Top Questionnaires for IT Vendor Assessment
Business partnerships require trust, but knowing which vendors you can trust to protect your customer's PII and PHI is difficult. With the rise of information technology, there are countless ways that trust can be broken, whether intentionally or unintentionally. As a starting point, you need additional information about information security policies, internal security practices, incident response and disaster recovery plans, and any past security incidents.
We Want You! Win the War on Ransomware Today
Arguably, the first malware extortion attack occurred in 1988 – the AIDS Trojan had the potential to be the first example of ransomware, but due to a design flaw, the victims didn’t end up actually having to pay up the 189 bucks. It’s safe to say that over the past 31 years, attackers have perfected the ransomware craft, with organizations shelling out more than $25 billion per year. We don’t expect it to end any time soon.