What Role Should Dependency Management Play as the Regulation of the Software Supply Chain Escalates?
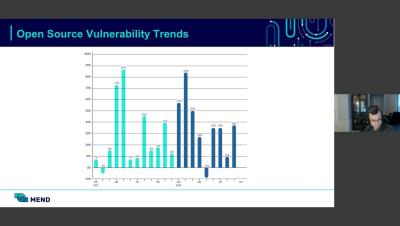
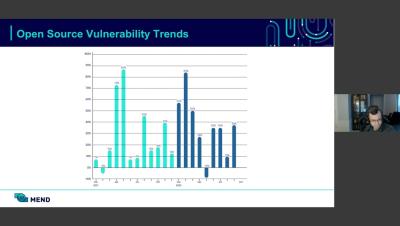
Two big trends are now converging that will change the way we view and implement software supply chain security and make dependency management a vital part of assuring security. Let’s look at why and how this is happening, and what it means for dependency management.