Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Sysdig
Customer Corner: "How BigCommerce Achieved Real-Time Cloud Security"
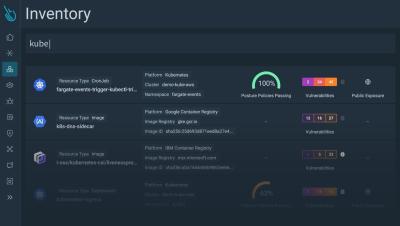
Strengthening Your Security with Agentless Vulnerability Management
Rethinking Cloud Security with Sysdig's CNAPP
Ensuring Compliance in an Ever-Evolving Cloud Security Landscape
According to CSO the fines incurred for data breaches or non-compliance with security and privacy laws, for only a handful of companies, has cost $4.4 billion. The global average cost of a data breach in 2023 was $4.45 million, a 15% increase over 3 years (IBM). The challenge for organizations is how to safeguard sensitive information while adhering to the law, but without compromising innovation. Cyber threats loom large, affecting businesses in every industry.
AWS's Hidden Threat: AMBERSQUID Cloud-Native Cryptojacking Operation
The Sysdig Threat Research Team (TRT) has uncovered a novel cloud-native cryptojacking operation which they’ve named AMBERSQUID. This operation leverages AWS services not commonly used by attackers, such as AWS Amplify, AWS Fargate, and Amazon SageMaker. The uncommon nature of these services means that they are often overlooked from a security perspective, and the AMBERSQUID operation can cost victims more than $10,000/day.
Scarleteel 2.0 and the MITRE ATT&CK framework
In this blog post, we will take a comprehensive dive into a real-world cyber attack that reverberated across the digital realm – SCARLETEEL. Through an in-depth analysis of this notorious incident using the MITRE ATT&CK framework, we aim to unearth invaluable insights into the operational tactics of cyber adversaries.
eBPF Offensive Capabilities - Get Ready for Next-gen Malware
It’s not a mystery that eBPF (Extended Berkeley Packet Filter) is a powerful technology, and given its nature, it can be used for good and bad purposes. In this article, we will explore some of the offensive capabilities that eBPF can provide to an attacker and how to defend against them.
LABRAT: Stealthy Cryptojacking and Proxyjacking Campaign Targeting GitLab
The Sysdig Threat Research Team (TRT) recently discovered a new, financially motivated operation, dubbed LABRAT. This operation set itself apart from others due to the attacker’s emphasis on stealth and defense evasion in their attacks. It is common to see attackers utilize scripts as their malware because they are simpler to create. However, this attacker chose to use undetected compiled binaries, written in Go and.NET, which allowed the attacker to hide more effectively.