Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Sysdig
How Financial Services Organizations Can Stay Compliant - Without Sacrificing Security
Fuzzing and Bypassing the AWS WAF
What's New - December 2023 Recap
Welcome to our December edition of the “What’s New in Sysdig” blog series. We decided to do a year in review for this monthly recap as we wanted to focus on a few key highlights the company went through the past 12 months. As we look at the past year, the landscape of cloud security has seen its challenges and evolution.
Honeypots with vcluster and Falco: Episode II
This is part two in our series on building honeypots with Falco, vcluster, and other assorted open source tools. For the previous installment, see Building honeypots with vcluster and Falco: Episode I.
The Power of Library-Based Vulnerability Detection.
With an ever-growing number of vulnerabilities being discovered annually, vulnerability management tools are rapidly evolving to handle and prioritize these risks. However, it remains one of the most overwhelming and time-consuming areas in cybersecurity. There’s still significant room for enhancement, especially in reducing false alerts and prioritizing genuine threats.
Is Traditional EDR a Risk to Your Cloud Estate?
Organizations are transitioning into the cloud at warp speed, but cloud security tooling and training is lagging behind for the already stretched security teams. In an effort to bridge the gap from endpoint to cloud, teams are sometimes repurposing their traditional endpoint detection and response (EDR) and extended detection and response (“XDR) on their servers in a “good enough” approach.
Why Traditional EDRs Fail at Server D&R in the Cloud
In the age of cloud computing, where more and more virtual hosts and servers are running some flavor of Linux distribution, attackers are continuously finding innovative ways to infiltrate cloud systems and exploit potential vulnerabilities. In fact, 91% of all malware infections were on Linux endpoints, according to a 2023 study by Elastic Security Labs.
What's New in Sysdig - October 2023
“What’s New in Sysdig” is back with the October 2023 edition! My name is Zain Ghani, based in Austin, Texas, joined by my colleague, Matt Baran, based in Los Angeles, California, to share our latest updates with you. The last few weeks have been really exciting at Sysdig.
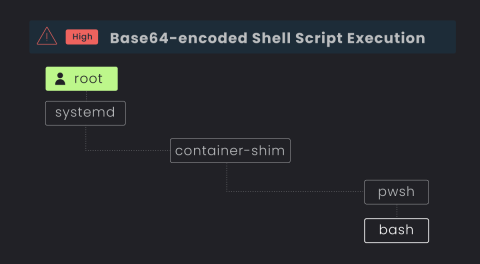
CVE-2023-38545: High Severity cURL Vulnerability Detection
On October 11 a new version of curl (8.4.0) was released, where a couple of new vulnerabilities were fixed (CVE-2023-38545 with severity HIGH and CVE-2023-38546 with severity LOW). These issues were previously announced in the project’s discussion. At the time of this blog, there have been several proof of concepts released for CVE-2023-38545 which result in crashes, but not exploitation.