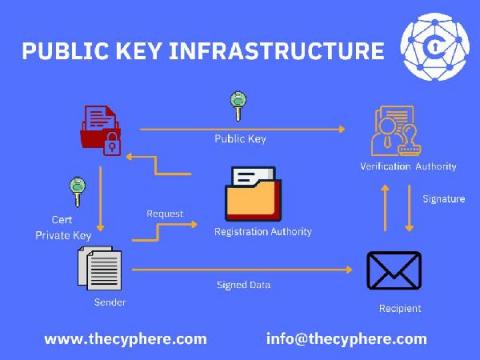
Public Key Infrastructure: PKI explained in simple terms
PKI stands for Public Key Infrastructure. It is the foundation of modern information security. PKI is a set of practices, policies, and technologies that protect sensitive data from unauthorised access or use. If you’re not using it yet, there are many reasons why you should be.