Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Encryption
The Best And Easiest Ways To Secure The Data In Your Company
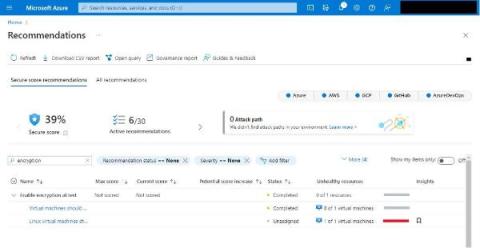
Easily Enable Encryption: Secure Cloud-native Development Series
Build secure cloud-native applications by avoiding the top five security pitfalls we lay out in our Secure Cloud-native Development Series. This blog is the fourth part of the series, and it will teach you why and how to easily enable encryption and save yourself headaches down the road. Here's a new motto: encrypt everything! When securely moving to cloud-native technologies, building encryption in from the start will save us a lot of headaches later.
What is a Code Signing within the Public Key Infrastructure (PKI)?
Public Key Infrastructure (PKI) is a fundamental backbone, empowering the seamless use of cutting-edge technologies like digital signatures and encryption across vast user populations. It encompasses a comprehensive suite of hardware, software, policies, processes, and procedures, working harmoniously to create, manage, distribute, use, store, and revoke digital certificates and public keys.
Cryptographically Relevant Quantum Computers (CRQCs) & The Quantum Threat in 2023
Secure Your Digital Footprint: Unleashing the Power of Email Encryption
In the digital realm, email communication has become the standard form of communication in our personal, work, and education. Due to the information we consistently send via email, they could easily fall into the wrong hands if left unprotected, bringing about dire consequences such as identity theft and financial losses. To avoid such nightmares, you can use a temporary email to keep your email safe from spam or an encrypted email to protect the contents of the emails you send.
Implementing TLS in Kubernetes
As cloud technology continues to evolve, the demand for Kubernetes is skyrocketing. As a result, security has become a top priority for developers looking to protect their application data. That's where Transport Layer Security (TLS) comes into play. TLS is essential for ensuring a secure connection between your applications and the internet. TLS leverages asymmetric and symmetric cryptographies to keep your data secure in transit and at rest.
The Secret's Out: Researchers Reveal Backdoor in Emergency Radio Encryption
For over 25 years, a technology utilized for vital data and voice radio communications globally has remained under wraps, preventing in-depth testing for potential vulnerabilities. However, a small group of researchers in the Netherlands has now shed light on it, uncovering significant flaws, including a deliberate backdoor.
Unveiling the secrets: Exploring whitespace steganography for secure communication
In the realm of data security, there exists a captivating technique known as whitespace steganography. Unlike traditional methods of encryption, whitespace steganography allows for the hiding of sensitive information within whitespace characters, such as spaces, tabs, and line breaks.