Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
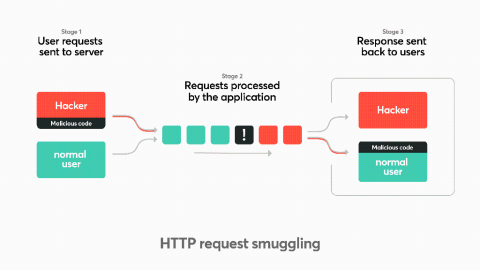
Hiding in plain sight: HTTP request smuggling
HTTP request smuggling is increasingly exploited by hackers in the wild and in bug bounty programs. This post will explain the HTTP request smuggling attack with remediation tips. HTTP request smuggling is an attack technique that abuses how two HTTP devices send requests between each other (typically a front-end proxy or a HTTP-enabled firewall and a backend server) or chaining multiple servers together with different configurations.
Detect reverse shell with Falco and Sysdig Secure
Reverse shell is a way that attackers gain access to a victim’s system. In this article, you’ll learn how this attack works and how you can detect it using Falco, a CNCF project, as well as Sysdig Secure. Sometimes, an application vulnerability can be exploited in a way that allows an attacker to establish a reverse shell connection, which grants them interactive access to the system.
SIEM vs. IDS: What is the Difference?
The main difference between a security information and event management (SIEM) solution and an intrusion detection system (IDS) is that SIEM tools allow users to take preventive actions against cyberattacks while IDS only detects and reports events. Security information and event management (SIEM) is an approach to cybersecurity combining: Note: the acronym SIEM is pronounced "sim" with a silent e.
Protect Citizens' Data with Netwrix solutions
Ask the Experts: The State of Industrial Cybersecurity
NetWalker Ransomware - What You Need to Know
NetWalker (also known as Mailto) is the name given to a sophisticated family of Windows ransomware that has targeted corporate computer networks, encrypting the files it finds, and demanding that a cryptocurrency payment is made for the safe recovery of the encrypted data.
How to Recover from API Downtimes and Errors
APIs are stable, until they aren’t. We talk about that often at Bearer. If you control the APIs, it gets easier, but with third-party APIs and integrations it can be more difficult to predict when an outage or incident is about to happen.
5 Strategies to Mitigate Business Risk During Coronavirus
Business risk in the United States may be higher during the novel coronavirus pandemic than at any time in our generation, making risk management a must. What are your strategies for risk mitigation—not only in your enterprise but up and down your supply chain—amidst COVID-19 disease outbreaks? Business interruption is a growing concern right now.
How malware mimics the spread of COVID-19
It’s a weird time to be alive. Millions of people globally are living under government lockdowns, as we collectively endure the COVID-19 pandemic. COVID-19 has brought to light some fundamental truths about humanity, including our deep-seated need for social interactions. It has also highlighted how reliant we are on critical infrastructure like our healthcare systems and internet connections, both of which are currently strained.