Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Stories from the SOC - Multi-layered defense detects Windows Trojan
Malware infections are common and are often missed by antivirus software. Their impact to critical infrastructure and applications can be devastating to an organization's network, brand and customers if not remediated. With the everchanging nature of cyberattacks, organizations need a layered security strategy. They shouldn’t depend solely on a single layer of security to keep them protected.
OWASP API Security Top 10 (With examples & fixes)
The OWASP, stands for The Open Web Application Security Project, is a non-profit foundation that works to improve application security by listing guidance such as top OWASP API security vulnerabilities and their prevention. Through community-led projects globally, it is a great source for tools, resources, education & training for developers and technologists to secure the web and mobile applications.
Detectify Security Updates for November 16
Our Crowdsource ethical hacker community has been busy sending us security updates, including 0-day research. For Asset Monitoring, we now push out tests more frequently at record speed within 25 minutes from hacker to scanner. Due to confidentially agreements, we cannot publicize all security update releases here but they are immediately added to our scanner and available to all users. The following are some of the security vulnerabilities reported by Detectify Crowdsource ethical hackers.
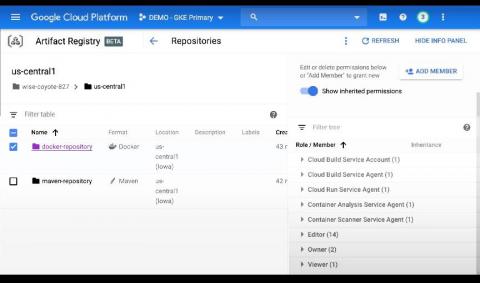
Sysdig extends image scanning to Google Cloud's Artifact Registry
In support of modern application development built on CI/CD, containers and open source, Google Cloud launched Artifact Registry (now generally available), a new artifact management solution. Sysdig helps DevOps teams using Artifact Registry confidently secure the build pipeline with comprehensive image scanning that identifies container vulnerabilities and misconfigurations to reduce risk.
Working From Home: Overcoming Lockdown Challenges | Netacea
Lookout is the leader in mobile security
Create a Zero Trust strategy for your mobile workers
Lookout for Small Business: Secure Your Growing Business with Enterprise-grade Security
Java Crypto Catchup
In 2017, we started a blog series talking about how to securely implement a crypto-system in java. How to Get Started Using Java Cryptography Securely touches upon the basics of Java crypto, followed by posts around various crypto primitives Cryptographically Secure Pseudo-Random Number Generator (CSPRNG), Encryption/Decryption, and Message Digests. We also released a Java Crypto Module for easier dockerization of injectable modules exposing Crypto services via an API.