Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Weekly Cyber Security News 22/01/2021
A selection of this week’s more interesting vulnerability disclosures and cyber security news. For a daily selection see our twitter feed at #ionCube24. Have to say, this article topped my list of cool vulnerabilities this week, nay, a few months I think.
Applying 3 Practical Lessons from the SolarWinds Breach
It’s been more than a month since the SolarWinds breach first started dominating security headlines, and we’re still learning new details about the attacks and the organizations affected. Even as the discussion quiets down, it’s easy to imagine we’ll still be looking back and analyzing the full effects of these incidents in much the same way we talk about other seminal breaches and security events from the past 20 years.
AppSec Bites Part 1: Balancing Speed and Thorough AppSec Coverage
In today’s world, speed wins. Just take Amazon for example. You can place an order with the click of a button and have it delivered to your door in under twenty-four hours. Retailers that can’t compete with Amazon’s speed are falling behind. The same level of speed and efficiency is expected with technology. Companies are in a race to deliver new and innovative technology first. But aside from speed, companies are also concerned about the security of their software.
How to cyber security: Faceplanting in 10 lines of code
Sometimes it’s hard to convince people that security needs to be part of every software development process. “We passed all our tests,” they might tell you. “Isn’t that good enough?” The problem is that functional testing usually focuses on the happy path—a place where users act rationally, systems behave well, and nobody is attacking your application.
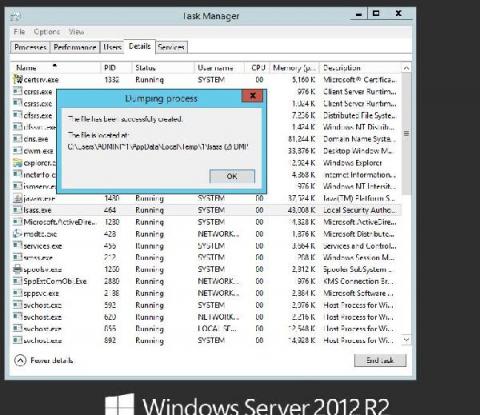
IT security under attack: Credential dumping attacks in Windows environments
Most of the time, threat actors in the cybersecurity landscape don’t employ advanced techniques and tools to intrude and establish a foothold within networks. Often, they disguise malicious operations by mimicking the activities of legitimate users, leaving behind little to no footprint. Blending malicious actions with day-to-day IT activities helps attackers maintain a low profile and remain undetected for a longer period.
Education, certifications, and cybersecurity
The question of cybersecurity certifications comes up very frequently on discussion boards. What is the best certificate to get? Is a college degree better for getting a cybersecurity role? What education or skills are needed for various cybersecurity roles? And many, many more. In this post, I'll try to clarify some of these questions and more.
API Security in a Digitally Transformed World
One unexpected consequence of the global pandemic is the acceleration of digital transformation across organizations of all sizes. With so many employees working from home, organizations realized they needed to upgrade to a cloud infrastructure to support everyone working remotely. As applications moved from on-premises to the cloud to support these new remote users, organizations needed to think about the APIs and microservices that connected users to essential applications.