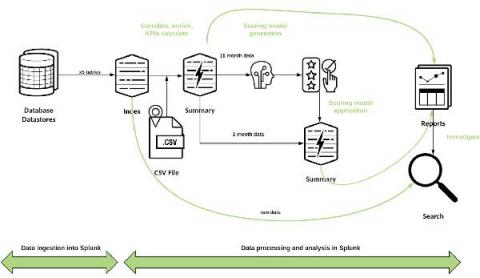
Creating a Fraud Risk Scoring Model Leveraging Data Pipelines and Machine Learning with Splunk
According to the Association of Certified Fraud Examiners, the money lost by businesses to fraudsters amounts to over $3.5 trillion each year. The ACFE's 2016 Report to the Nations on Occupational Fraud and Abuse states that proactive data monitoring and analysis is among the most effective anti-fraud controls.