Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
ManageEngine
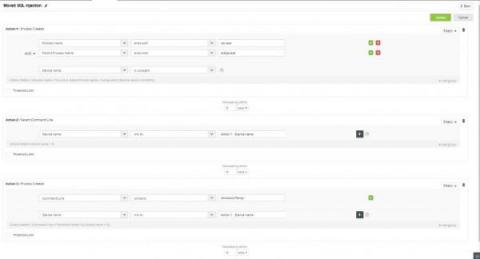
PAM Masterclass - Episode 6: Exploring PAM360's contextual integrations - Part 2
Five worthy reads: What's cooking between cookie consent and user privacy?
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week we explore website cookies, their role in managing user identity and behavior, and the key ingredients to a safe cookie policy. There’s no worse way to enter a website than to be met with a cookie consent encounter. But how many of us click “Accept All” without much thought, just to rid ourselves of the interruption?
The MOVEit Transfer vulnerability affects 40 million people worldwide
In over 600 data breaches, 40 million individuals were affected across the globe due to the MOVEit Transfer vulnerability. Between June 2023 and the present day, healthcare information, educational records, financial records, personal information, Social Security numbers, and insurance details have been either stolen or wiped out by threat actors who abused the MOVEit Transfer vulnerability.
Adopting the 5S strategy in cybersecurity
The 5S strategy has long been considered a reliable approach to workplace organization. Originated and developed as a strategy to facilitate just-in-time manufacturing in post-war Japan, 5S is widely used today to improve efficiency and overall productivity across many industries. Companies known for their precision, discipline, and attention to detail, such as Toyota, have extensively implemented the 5S methodology to promote clutter-free, organized, and regulated work environments.
7 best practices for deploying OS images
Five worthy reads: Strengthening cybersecurity-exploring vital legal provisions
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week we are exploring vital legal provisions to strengthen cybersecurity. The digital environment has developed into a fertile ground for cybercrime in today’s connected society. Governments all across the world have realized the need for extensive legislative protections for people, organizations, and national security due to the increase in cyberattacks.
ManageEngine Recognized as a Customers' Choice in 2023 Gartner Peer Insights 'Voice of the Customer': Security Information and Event Management (SIEM) for the fourth time
We’re thrilled to announce that ManageEngine has once again been recognized as a Customers’ Choice in the 2023 Gartner Peer Insights ‘Voice of the Customer’: Security Information and Event Management (SIEM). This marks the fourth time that ManageEngine has been recognized as a Customers’ Choice, which we believe is a testament to our commitment to providing our customers with exceptional SIEM solutions.
Five worthy reads: Cybersecurity in the age of AI - Battling sophisticated threats
Five worthy reads is a regular column on five noteworthy items we have discovered while researching trending and timeless topics. This week we are exploring the significant role of AI in the field of cybersecurity and why it’s the next biggest thing in cybersecurity.
Comprehensive visibility is the foundation for effective threat detection and response
Businesses today are more dependent than ever on technology, making strong threat detection and response strategies essential. Cybercriminals in the modern world are constantly looking for new and creative ways to hack into organizational networks and steal sensitive data. Comprehensive visibility is a crucial element that is sometimes paid less attention to yet is the foundation of efficient threat detection and reaction.