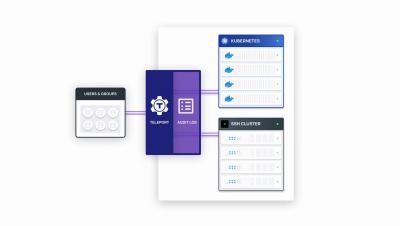
Building and Evaluating a Threat Intelligence Program (Part 2)
In the second part, we will take the discussion forward from where we left in the first part. Earlier, we have discussed the basics of threat intelligence and its types. In this post, we will discuss various considerations while building a threat intelligence plan.